Cisco Wrong Credentials. Please Login Again.
Managing user Accounts and passwords in Cisco IOS Devices is very of import task. With several unlike user accounts, y'all tin can also set different privilege level for each i of them. Unlike privilege means dissimilar bachelor commands that can be executed per user account. In this commodity, we will get deep on creating users accounts and all its features including privilege, encryption, and automation that nosotros can implement in Cisco IOS devices. This article shows how yous tin manage user accounts and passwords in Cisco IOS devices.
Manage User Accounts and Passwords in Cisco IOS Devices
Basically you will need to create at least a user business relationship in your Cisco router or switch if:
- You lot desire to secure the console command line
- Yous want to enable virtual last line such every bit telnet or SSH
- You want to restrict some commands to a specific user
- You want to enable automation to some IOS commands

The standard control to create user account and password in Cisco IOS is shown in the example below, and it must be executed in global configuration mode.
GeekRtr(config)#username admin countersign letmein123
With above configuration you have successfully created username Cisco IOS device. All the same, there is i major weakness in this configuration and information technology will be explained in this sub-section below.
Securing your Cisco IOS password with encryption
When you lot define a password, it is stored with clear-text format in your running-configuration. In the show running-config output, the password will be shown as it is:
GeekRtr#show running-config | include username username admin password 0 letmein123 GeekRtr#
Notice that your password phrase is explicitly written there. Also notice the number "0" earlier the passphrase indicates it is unencrypted. Information technology'south never a skillful idea to leave your countersign in a readable condition similar this.
To solve this consequence, we can apply encryption to the password and hide the exact passphrase. There are two types of encryption:
Encryption type 7
With the command service password-encryption, all existing and hereafter added passwords will be automatically encrypted.
GeekRtr(config)#service password-encryption GeekRtr(config)#do prove running-config | include username username admin password 7 10420C0D08121B055D5679
Every bit you tin can see above, password phrase in the prove running-config output has been masked past a random numbers and letters. Too notice that the number "0" before the passphrase has been changed to "vii", indicating it has been encrypted using type 7 hash. However, this encryption is no longer secure in today'south network every bit it tin can be hands reversed to reveal the original passphrase.
Encryption type 5
Instead of type vii, information technology is highly advised to employ encryption type 5. It using MD5 algorithm to hide your original passphrase.
MD5 algorithm is a complex one-style performance and it'southward nearly impossible to opposite the process. It'south far stronger than encryption type 7 and the merely way to reveal the original password is by using brute force (and of course it would take a lot of fourth dimension and resources just to exercise that — depends on the original passphrase length).
To use blazon v encryption to secure passwords in Cisco IOS devices we can merely create username followed by a clandestine instead of password. The configuration will be demonstrated in the side by side example merely first we volition delete the username and password created earlier:
GeekRtr(config)#no username admin
And with this configuration we will copy username using a hole-and-corner:
GeekRtr(config)#username admin secret letmein123 GeekRtr(config)#do show running-config | include username username admin secret 5 $ane$rszA$h4AZMOUECxMMoBg/BVnm//
At present you can see that by specifying a hush-hush instead of countersign, it volition automatically replace the phrase with random characters combined with random uppercase and lowercase letters, making it totally not-readable to homo's eyes. Discover the number "5" before the encrypted passphrase in the bear witness running-config output above — indicates that you lot have secured your password using type 5 encryption (MD5).
Applying user accounts to console command line
The user account we created earlier is basically useless if we don't enforce login procedure. In this section we will enforce login to the console command line.
GeekRtr(config)#line con 0 GeekRtr(config-line)#login local
By issuing control login above, nosotros told the device to ever inquire credential to whatever attempt of accessing the console control line. The word local is telling the device to look upwards its internal user account database for hallmark, which means the device will refer to the list of username we created before. Now the device will ask for login credential on the side by side effort of accessing CLI via console line.
GeekRtr con0 is now available Printing Render to get started. User Admission Verification Username:
Securing privileged EXEC mode
By default subsequently login you will be prompted with the device hostname followed by a ">" sign, indicating that you are inside the user EXEC mode. You cannot enter configuration mode except from privileged EXEC style. To enter privileged EXEC mode from user EXEC style, simply utilise command enable. The "#" sign adjacent to the device name indicates y'all are in privileged EXEC mode.
GeekRtr>enable GeekRtr#
Now of course we don't desire anybody to easily enter the privileged EXEC style. With the configuration below nosotros will fix authentication on any endeavour to enter privileged EXEC mode using the enable command:
GeekRtr(config)#enable hugger-mugger letmeconfig123
Note: remember that by specifying secret instead of password volition encrypt the passphrase in configuration file using type 5 encryption, so always utilise secret whenever possible.
Every bit the result of this configuration, now a passphrase will exist asked before we entering the privileged EXEC mode.
GeekRtr>enable Password:
Applying username to virtual terminal line (Telnet/SSH)
We can enforce login on the remote access with similar configuration as the one we applied in the console line (anyway, information technology is mandatory to have username and password in terminal line if we desire to enable SSH) With this configuration below nosotros will enforce login to virtual final line:
GeekRtr(config)#line vty 0 4 GeekRtr(config-line)#login local
An enable-countersign might as well be required in order for virtual terminal access to work, you lot can refer to the previous sub-section titled "Securing privileged EXEC style" to create an enable-password.
Assigning privilege to specific user accounts
By default all user accounts are created using privilege level ane and it is equivalent with user EXEC mode. When we employ the command enable, we volition exist granted with privilege level 15 by default, and privilege level fifteen has admission to all configurations and commands. We can create custom privilege level between 1 and 15. By default if nosotros assign any privilege level to a user account information technology will bypass the user EXEC mode.
In this example we are going to create a new user account with privilege level seven.
GeekRtr(config)#username junior_admin surreptitious letmetry123 GeekRtr(config)#username junior_admin privilege 7
In this example, if we try login using junior_admin nosotros will exist brought direct to privileged EXEC mode. But as you tin see in the screenshot beneath, the command configure terminal that we use to enter global configuration mode is not recognized.

This is because nosotros haven't ascertain what commands are allowed to exist executed using privilege level seven. Now in this example we will allow everybody with privilege level vii to practice something at the interface level, which is giving a description. Nosotros'll exist back to login using our standard admin account (the one with privilege level xv) and configure it this manner:
GeekRtr(config)#privilege exec level seven configure concluding GeekRtr(config)#privilege configure level 7 interface GeekRtr(config)#privilege interface level seven description
In the offset line of the to a higher place config, nosotros're allowing users with privilege level 7 to use command configure terminal in the privileged EXEC mode and enter the global configuration mode. Then the 2nd line volition allow them to enter interface configuration mode from global configuration mode by issuing control interface interface_name . Then finally the third line will let them to configure the interface description. Below is the upshot:

Notice that junior_admin can now enter global configuration fashion and interface configuration style consecutively. But also notice that the other interface level commands except description are non shown in the help context, and that ways junior_admin cannot alter annihilation except the interface description; considering we configured it that way!
Applying automated command to a specific user business relationship
Basically we apply automatic command to a specific user account because nosotros want a dedicated user account to execute a control. In this example nosotros are going to create a user account named view_ip. Only like the name says, this user account is dedicated to meet IP address of the device interfaces. We will configure it to automatically execute control bear witness ip interface brief after logon.
GeekRtr(config)#username view_ip underground v13w_1p! GeekRtr(config)#username view_ip autocommand show ip interface cursory GeekRtr(config)#username view_ip nohangup
Note: we also added the parameter nohangup to forestall session disconnected after autocommand executed
Beneath is screenshot of the consequence:
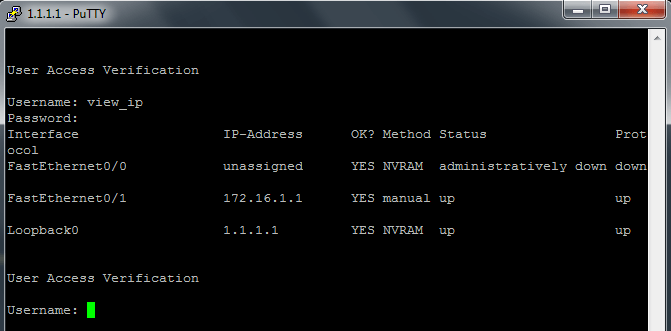
In this style you can manage user accounts and passwords in Cisco IOS Devices.
The post-obit 2 tabs change content below.
- Bio
- Latest Posts
![]()
I am Information technology practitioner in real life with specialization in network and server infrastructure. I have years of experience in design, analysis, functioning, and optimization of infrastructure solutions for enterprise-scaled network. You can send me a message on LinkedIn or email to arranda.saputra@outlook.com for further inquiry regarding stuffs that I wrote or opportunity to collaborate in a project.
![]()
Source: https://www.mustbegeek.com/manage-user-accounts-and-passwords-in-cisco-ios-devices/
0 Response to "Cisco Wrong Credentials. Please Login Again."
Post a Comment